Section Navigation
Introduction
Students will build the required skills to avoid being subject to an online scam. There are many scams and being deceived is easy. Having critical literacy and online skills helps users recognize the characteristics of scams and cyber criminals, and ultimately avoid being scammed online.
Learning Goals
By the end of the module students will have a general understanding of online scams and will have a critical eye when viewing suspicious material.
Vocabulary
Scam - a dishonest or fraudulent scheme.
Phishing - emails pretending to be from a reputable source in order to obtain important and private information from individuals.
Malicious - intending harm.
Operating System - the software that supports the computer’s basic functions.
Malware - software that is intended to damage or disable computers or computer systems.
Catfish - to lure someone into a relationship by means of a online persona.
Guiding Questions
- Have you ever followed a link in an email that seemed suspicious?
- Have you ever received a text or an email that said you won a trip or money? Did you believe it?
- Does anyone have any personal stories about either themselves or a friend or family member who was scammed online?
Curriculum Links
Critical literacy can be related to the English curriculum and any subjects that include media. As students spend more time online, it is increasingly important they have a critical eye that they can apply to the various online materials they consume, and ultimately avoid being scammed.
Materials
- A projector and speakers
- Paper and a pen or pencil
- Computers (or other devices)
- OpenShot – Download OpenShot
- Kahoot (optional) – Visit Website
Non-Computer Activity
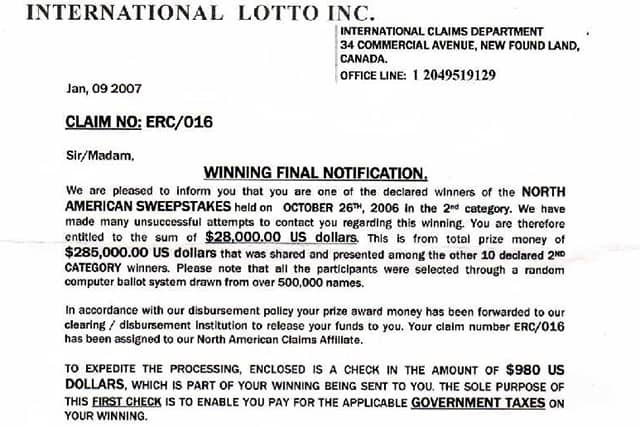
Review the following letter that is an example of a lottery scam. Read through the letter and have students identify what looks suspicious about the letter and how a reader could identify this is a scam (answers could include the letter does not address the person by name, return address is incorrect, there is a sense of urgency)
Activity
Lead a group discussion about the sharing and protection of private information. Would you ever share your internet passwords with strangers? Online passwords protect private information and it is very important to keep passwords secure. Sharing this information is like giving a stranger the keys to your house.
Watch one of the following videos from Jimmy Kimmel where people share their passwords on TV.
Discuss how easy it was for these people to be tricked into sharing their passwords. Do you think you could be tricked to share your password or other important information? Why is it important to keep personal information to yourself?
Computer Activity
Unlike the Jimmy Kimmel video where people were asked directly, cybercriminals will try to get your information in less obvious ways such as enticing you to click links and download items. We understand how to protect our information from people we encounter in person (such as shielding your hand when entering a PIN), but protecting our information online takes a different kind of vigilance. We will learn about common scams and how to protect ourselves, and then will create videos to share this knowledge with others.
Activity
Have a group discussion about online scams. What online scams do you know about? How can you protect yourself from these scams? After the students have generated some ideas, refer to this list from Heimdal Security of the top online scams to avoid in 2018.
The following are a few of the scams mentioned in the article:
- Phishing Email Scams: One of the most common ways to have your online security breached is through malicious attachments in emails. In many cases phishing scams try to trick people into sending important information such as banking information or passwords. These messages appear to be from official sources such as banks, legitimate companies or social media representatives. These messages sometimes include a story that requires your response urgently. To protect yourself from phishing scams do not click links found in suspicious emails and never share important information over email. Banks and companies typically do not request private information via email. If you are in doubt, call the company instead of sharing information online. Do not use the telephone number provided in the suspicious email; use the number from a bill or the official company website.
- Greeting Card Scams: Another common scam involves a digital greeting card. This is usually done through a link received in an email or message. Once the link is clicked malicious software is downloaded and installed on your operating system and used to gain valuable information. To protect yourself, do not click suspicious links, and consider purchasing a security protection program for your computer. Some examples include Norton Security Standard, Kaspersky Total Security 2018 and McAfee Total Protection.
- Bank Loan or Credit Card Scam: Credit card scams are on the rise as more people are deceived by bank offers that seem too good to miss. They usually include an offer of a large amount of money with a pre-approval and require you to “only” pay for processing fees. Ask yourself “how can a bank offer me such a good deal or large amount of money without doing a credit check?” To avoid falling victim to these scams think critically about what is being offered and monitor your accounts closely. If you want to know more about an offer call the company directly.
- Lottery Scams: This is another common scam that comes in an email informing you that you have won a large sum of money and to access it you “only” need to pay processing fees. Again, be cautious of information that sounds too good to be true, don’t click suspicious links, and don’t share information online. Be wary of paying any fees online that are supposed to give you access to more money.
- Online Dating Scams: Online dating scams happen through various social media accounts. Typically, the male scammers are from West Africa, and the female scammers are from Eastern Europe. The scam involves meeting someone online and them requesting money to help them buy a ticket to come visit you, or because they have financial troubles. Always avoid sending money online to people you have never met or don’t know very well even if they appear to have good intentions. Online dating scams are an example of Catfishing.
- Fake Antivirus Software: Usually this scam starts with an alert or pop-up that says your computer has been infected and you need to click the link to download antivirus software to protect your computer. These messages can appear legitimate and look similar to other security products. Downloading this fake antivirus can lead to pop-ups, or cause your computer to be infected with malware. Do not click any links in pop-up windows that tell you your computer has been infected, and only apply updates from legitimate sources. Also, only download anti-virus protection you have purchased from reputable sources such as Norton or McAfee.
- Facebook Impersonation Scam: Facebook is the most popular social media network, which makes it the perfect place for online scams. If a friend has been exposed to a virus or malware, they can be host to scams without knowing it. An example is a video from a friend, that does not seem like something they would normally send; do not open messages that look suspicious. To protect yourself, do not accept friend requests from people you don’t know, and do not forward suspicious messages. You can also protect yourself by not sharing passwords and avoiding connecting to public or free Wi-Fi networks.
It is important to reiterate that cyber criminals will use all sorts of tricks to fool people. For example, they may use cultural symbols, country flags or items of spiritual connection that people have a familiarity with because of their own faith, cultural practices and upbringing. It is important to be wary in this situation, even though the language and imagery used appeals to your sense of trust; it is ultimately a cleverly designed false narrative, aimed at making you lower your guard.. Scammers will use this cultural familiarity as a tactic to try and gain trust from those they are trying to deceive. That is why it is always good to check sources and consult with family, community members or any trusting adult before making any contributions online or clicking on any links you’re not familiar with.
Now that we know more about online scams and how to protect ourselves, we will work in small groups to create a video to share this information with others. In your video you could show someone attempting an Internet scam in-person to demonstrate how we wouldn’t share private information with strangers, therefore we shouldn’t share it online. Another strategy could be to make an informative “how to” video that explains how to protect your online privacy. For example, a stranger tells you in person that you’ve won a free trip but can only get the trip if you give them your name, age, address and passwords. By demonstrating how unbelievable this interaction would be in person, may help people think twice about being deceived in the same way online.
If you need to edit your video use the OpenShot Video Editor software. This will allow you to cut and trim videos as needed and give you the flexibility to piece together multiple shots, rather than feeling limited to taking the video in a single shot.
Conclusion
Have each group create a short quiz, five to ten questions, to test the knowledge of the other groups. Have the groups take each other’s quizzes, mark them, and compare results. If students have access to Internet they can make their quizzes on Kahoot to allow other groups to play.
Resources
- Media Smarts is a site about digital and media literacy. They have an article that looks at online privacy and how it is important not only to adults, but youth as well.
- Reader’s Digest has an article on popular online scams and how to avoid them.
- The ICPEN (International Consumer Protection and Enforcement Network) has great information on avoiding online scams based on the country you select. They also have videos about the importance of being aware of online scams.
- The Government of Canada has an Anti-Fraud Centre that offers support and guidance if you have been scammed. The site also has information on recent scams.
- Time has an article on one of the more recent Facebook scams, cloning.
- AARP has an article that explains Facebook scams and how they work. They also provide information on how to protect yourself from these scams.
- The Guernsey Financial Commission has great information on banking related online scams.
- Norton has an article that explains how to teach your kids about online scams.
- Crucial has an article on how to avoid web fraud and gives additional resources for avoiding specific types of online scams.
- iKeepSafe and Google has put together this document (PDF) that includes lessons on how to teach students to identify online scams.
- This is a good youtube video on using OpenShot Video Editor for basic video editing.
- An interesting article by Time “Do You Know How Much Private Information You Give Away Every Day?”




