Introduction
With the internet, the responsibility to protect one’s privacy and safety largely falls on the individual user. The more you engage and interact on the internet, the higher the chances that your privacy and safety could be violated. By creating an email account, the unfortunate reality is that you are now at a greater risk of a security breach:
- Someone could gain access to your email account, read your emails, or send emails in your name.
- Your emails could be read by the email service provider itself.
- You could receive an email intended to trick or scam you out of money or information.
In this section we will examine a few of these common security issues and some of the ways you can protect yourself.
Passwords
Email and other online accounts typically require passwords to keep your account secure, and ensure it is only accessible by you.
When you’re using an email service your computer is “talking” to another, the computers recognize each other as computers, but can they really tell if the other computer is who it claims to be? This reminds me of Inuit folk stories where an animal wears a human skin to interact with people, a famous example being Kiviuq and the Fox Woman. Changing skins is a common theme in these folk tales, but wearing another skin only becomes a problem when the animal intends to play a trick, or is deceptive about who and what they are. How can we trust it?
To avoid this potential problem of computers wearing other skins, the best way to ensure a computer is who it claims is to have a secret password for protection. This idea of “wearing a skin to mask a true identity” helps explains not only passwords, but many other security issues online, because hidden identities are often the first step in how scammers trick us or gain access to our private information.
Strong passwords
Passwords are an important way to maintain privacy online, but they’re not perfect. If someone knows a lot about you they might be able to guess your passwords. When a password is easy to guess it’s called a weak password.
If this is the case, what makes a password strong?
The standard advice is to make a password random, and include numbers and special characters that are not part of the regular alphabet. For example, “9anV2^^Lk[)5”.
More recent advice is that longer passwords are better than random passwords. But randomness is still important. For example: “The Northern Lights are bright tonight” is long, but not random. A good approach is to choose full words to make the password long, but ones that don’t relate to each other. For example: “The Northern Lights Soccer Tuktu Macaroni and Cheese”.
The a popular webcomic online, xkcd, made a humorous observation about password strength:
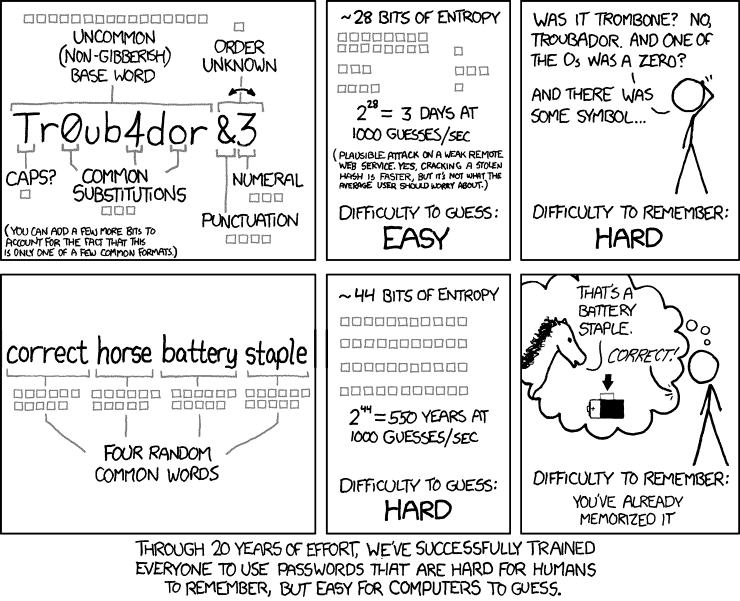
The joke is that random passwords are hard to remember, but easy for computers to guess. It’s funny and true at the same time.
Another problem with passwords is the number of sites that require them. We could use the same password for each, but if someone found out our password they could access all of our various accounts. Therefore it’s best practice to have a unique password for each separate account. This itself becomes problematic as it creates a lot of passwords to remember.
Advanced Tip: A modern approach to keeping a variety of strong passwords is to use a password manager. Password managers remember all of your passwords, so you only have to remember a single password for the manager itself. Learning to use password managers is beyond the scope of this module, but here is a good article if you want to find out more.
Forgotten passwords
What happens if you forget a password? How do you log in?
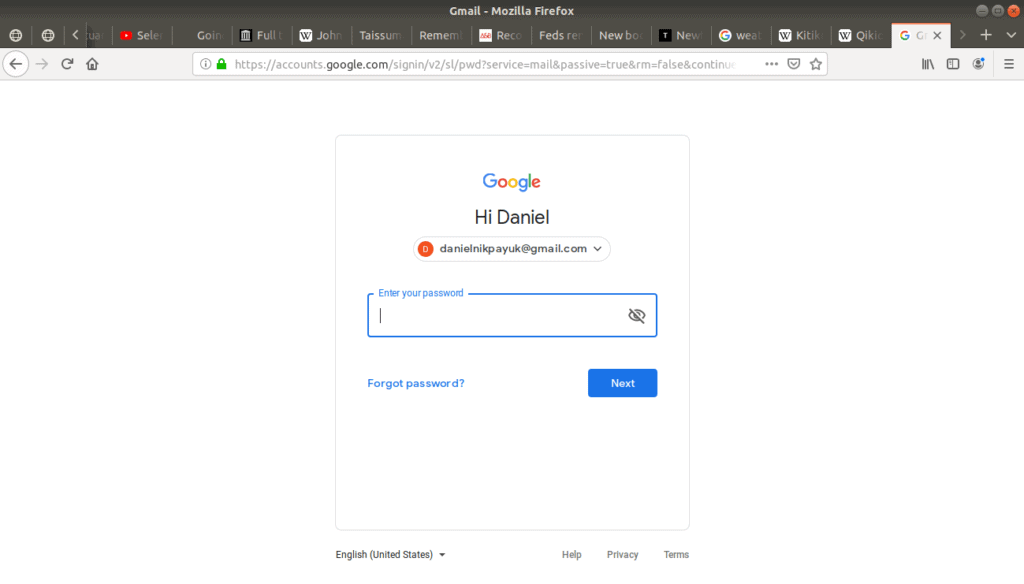
Online services which require passwords have a password reset tool:
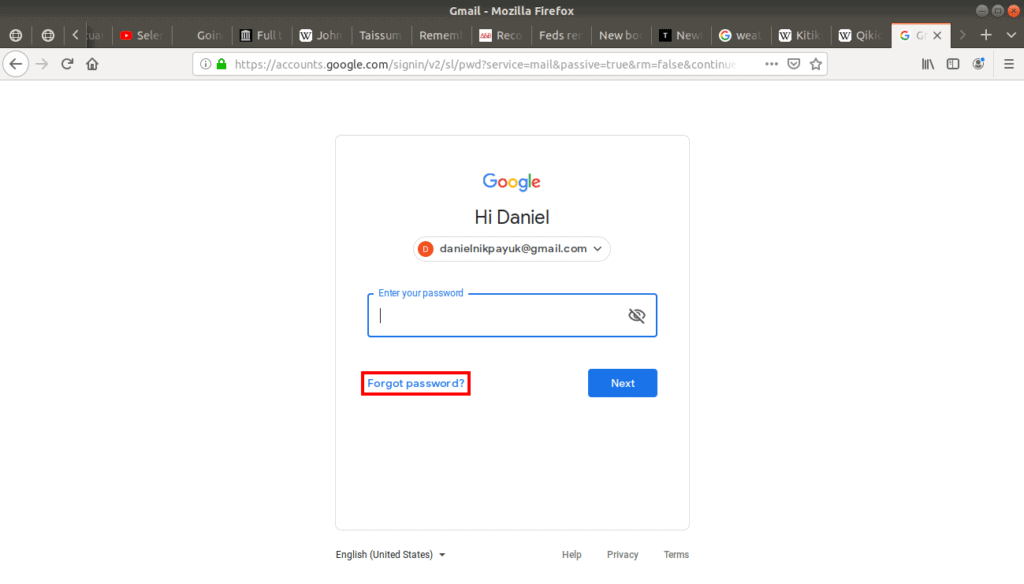
In the case of Gmail, this tool is called account recovery, but whatever the wording, when you click the Forgot password? link, it redirects you to this tool to help you get back into your account:
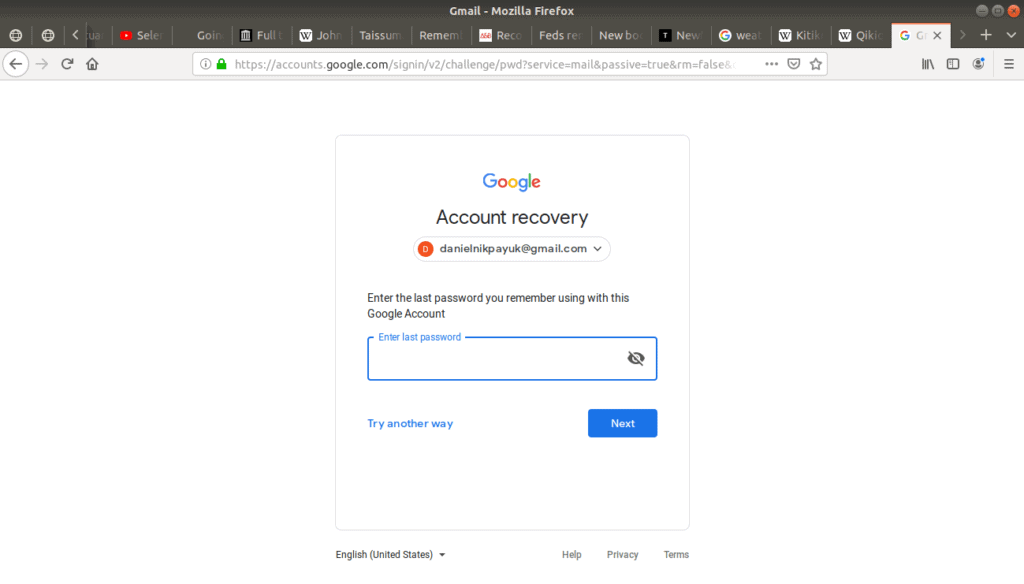
You then have to prove your identity in order to reset your password. The formal word for this is called authentication.
There are a few common ways to authenticate, called factors. Many factors of authentication are based on information that only you and your service know, such as a password, or other unique information.
The account recovery page asks us to enter the last password we remember. This is an authentication factor. If you’ve had your email account for a while, it’s a good habit to change your passwords occasionally. Gmail remembers your previous passwords, but it’s unlikely others would know them, so this is one way Gmail can be confident of your identity.
If you don’t remember any previous passwords, you can Try another way:
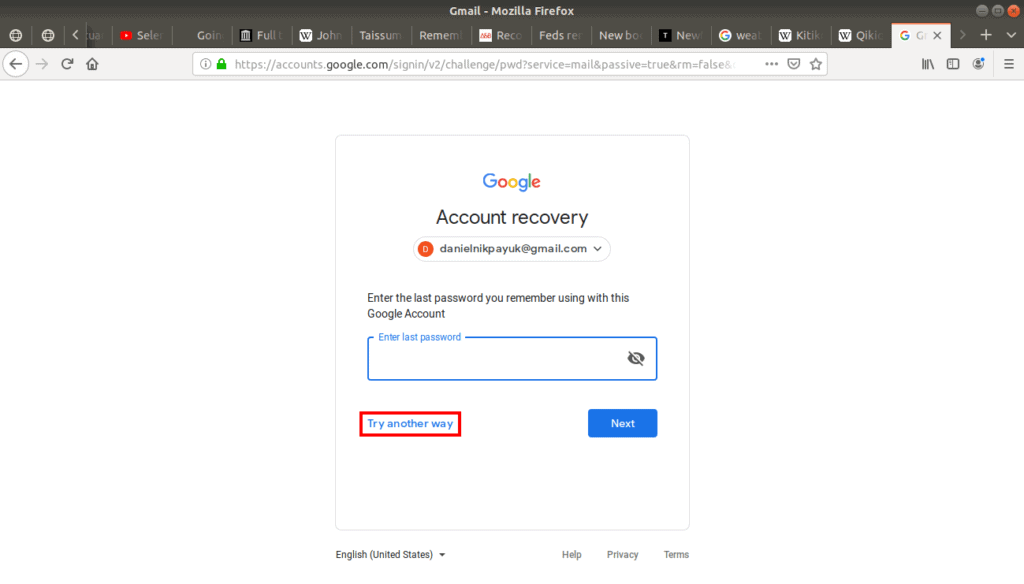
When you try another way you are prompted with another question:
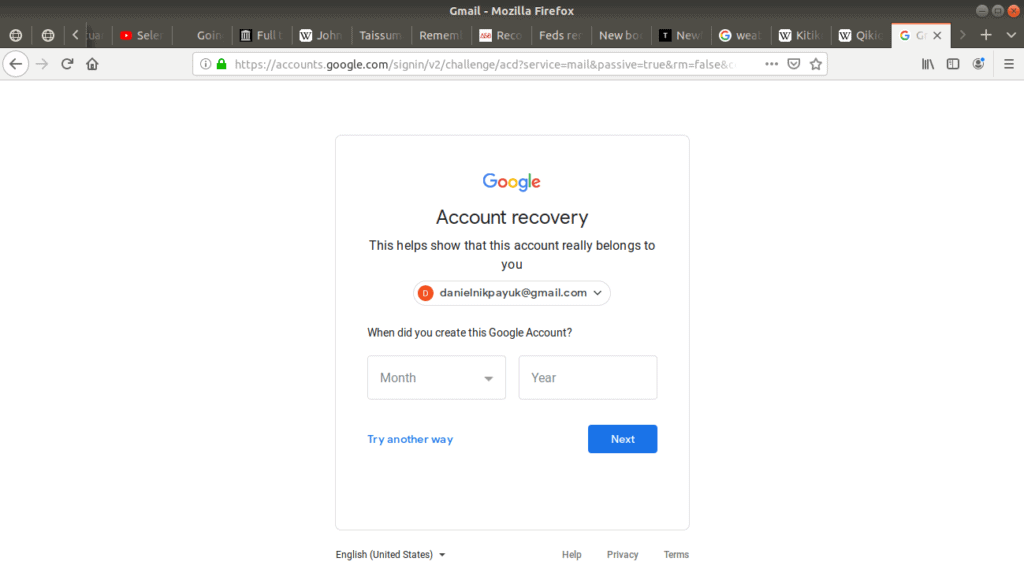
Gmail asks for the month and year you created your account. If you don’t remember this either, another type of authentication is to provide the service an alternate email address, to which the service can email a secret code. The idea being that since you are the only one who can access your other email, the service can be confident it’s you when you relay the code they sent:
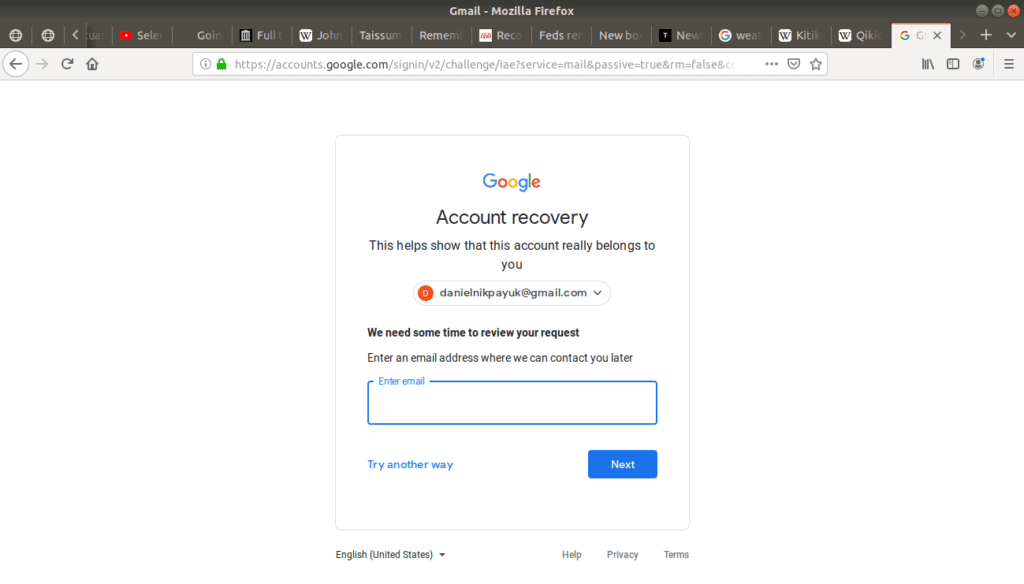
This type of authentication is based on the idea that someone else (or another service) who can be trusted is vouching for you. Another example of this is providing your cell phone number so the service can text you a secret code. After all, you should be the only one who can access your phone, right?
Another approach currently popular with security experts is called two-factor authentication. This simply means you have to prove your identity with two factors, for example, your service might send you a text and ask you a secret question. The thought is that two factors should be very difficult for others to fake.
Advanced Tip: Some services require two-factor authentication, but others provide it as an option within your account settings.
Account Privacy
Another issue with privacy is when the email service itself becomes disrespectful of your personal information.
When you send or receive an email it is always uploaded to the service provider’s computers first. We trust them to protect our emails from others, but they themselves have access to our mail, and in order to use their service we have to agree to their terms, even if that means sacrificing some of our privacy.
A person’s privacy is very important. Here are just a few reasons why protecting privacy is important. When people have their privacy violated:
- they can be overwhelmed with feelings of shame and embarrassment. No one should be made to feel that way.
- personal information could be made public that hurts their social standing within their community.
- it could limit or restrict a person’s access to the justice they seek.
This last point might not be obvious, so I will elaborate with some strong examples:
- authoritarian governments stay in power by preventing people from challenging their leadership. If they had your private information, they could threaten to expose it for compliance.
- insurance companies could take your private data and use it to reduce the social safety net you have with them.
Email services don’t give your private information away, but they do have access to it, therefore other agencies could gain access to it as well.
As for service providers reading our emails, why are they interested in doing this in the first place? There are a few reasons, but two of the biggest ones are:
- to determine if an email is spam and direct it to the appropriate folder in our account or warn us that it might be a scam.
- to improve their business by targeting the advertisements they show us.
When these services access our private information it’s unlikely they have harmful intentions, but since their ultimate goal as businesses are to make money—perhaps sometimes they get carried away and forget to be respectful of us, their users.
As for advertisements, how does this relate to our mail? Gmail is owned by Alphabet, which also owns the Google Search Engine, the Chrome Browser, and YouTube. Each time you visit any of these sites, Alphabet observes your online behaviour. I will use a hunting analogy to explain why they do this and how it helps them target their advertising.
When these services observe our behaviours, in many ways, it’s as though they are hunting us. By observing us they can understand and better predict what we like, what we dislike, and our habits. They’re not hunting us directly, but the potential money they could make from advertising to us.
If we are extend another analogy to the money: the money is like a pod of whales. Traditional wisdom says you don’t hunt the entire pod as it would collapse, which would ultimately hurt the whales and the hunters. Similarly, if these online services tried to take all our money at once, they’d advertise to us too much, and too randomly, and we’d probably stop using their services. Instead, they cleverly and subtly advertise to us, with special ads made just for us. This allows them to keep making money, and they do all of this by studying our private data.
Tip: Dy drawing these comparisons it is not my intention to be disrespectful to people trying to make a living for themselves. I just want to explain why our personal information is so important to these businesses, how it benefits them, and why we need to be vigilant about what we share online and to take responsibility for our privacy online.
Advanced Tip: If you’d prefer to keep your privacy but still want to use an email service, there are providers which offer end-to-end encryption, such as ProtonMail. These providers turn your email into a secret code that only you and the person you’ve emailed can read. The email provider still puts your email on their computer, but it looks like gibberish to anyone trying to read it. Then, the recipient gets it in its original form, so that they (and only they) can read it.
Scams
Having an email account potentially exposes us to scams. In a scam you may be asked for money or personal information, and with enough information, someone else could pretend to be you. This is called identity theft. An identity thief could open up a new credit card in your name, or any number of various accounts, putting you on the hook for the payments.
Advance fee
One of the most famous scams is the Nigerian Prince scam, where someone emails you claiming to be a Nigerian prince in a bad situation, and if you send them money or some of your personal information they will pay you handsomely once their situation improves. It is unlikely you will receive this exact email scam these days because it is so well known, but there are some variations to watch out for. The above link has good details about this.
Phishing
Scamming is all about trust: the more a scammer can get you to trust them, the more they can scam from you.
Scammers know it takes a lot of work to build trust with someone because relationships take time to build. This is why Nigerian Prince scams aren’t as popular. But if scammers pretend to be someone you already know and trust, you will be faster to let your guard down.
The word phishing comes from the English word “fishing”. The scam works in a similar sense where the scammer wants your personal information, but instead of asking for it directly in the email they send emails offering “bait” hoping you will bite.
A common phishing scam is known as irregular activity phishing. A topic we haven’t discussed is online banking, where customers go online to perform many of their banking transactions.
With irregular activity scams, you may receive an email from someone pretending to be your bank that states your account has had some “irregular activity” and you need to verify some personal information before you can access your account again. You can see an example of this here.
Within this email the scammer provides a hyperlink that opens a login page that appears official, but isn’t. And when you enter your personal information they have now stolen it from you. If you’re interested in more examples or other kinds of phishing scams there is an archive of them here.
I was recently sent an email that was flagged by Gmail as a possible phishing scam. It was actually from a friend who used a different email address than was previously used. This warning is a helpful feature of email service providers.

Hacking
A good rule to follow is to never click on any email links unless you’re absolutely certain they’re safe. You could be sent to a fake site, or you could get hacked.
In a way, hacking is like a scam, but for your computer. Instead of you being tricked, a hacker tricks your computer into granting access to parts of your its memory where you may have private or personal information.
In addition to links, it’s also a good rule to never open any email attachments unless you absolutely trust they’re safe. The unfortunate thing is, even if you trust the email account of the sender, it’s possible their account was hacked and used to send the scam email.
Account Activity and Review
When we created our account, you may have skipped reading the Privacy and Terms, which is a rather long document to read:
If you want to review or change some of your privacy options, you can access them from your Google Account; the same menu in the upper right where we sign out:
This opens your account manager, which has more detailed menus and options:
From here you can access the Privacy and personalization menu:
and it’s on this page that you can look at your privacy terms and options in more detail. You can even look at some of your account’s activity and history, such as when you last logged in. This could be a useful way to find out if someone has stolen your password and has logged into your account, for example.
Unfortunately, there are too many of these privacy options to explore in detail in this module, but every email provider has a way to reach these settings to review or change them.
Deleting Your Account
If you decide you no longer want to use the email account you’ve created, you can always delete it.
You can access this option from the same Privacy and personalization menu used above:

From here, scroll down to Delete a service or your account option:
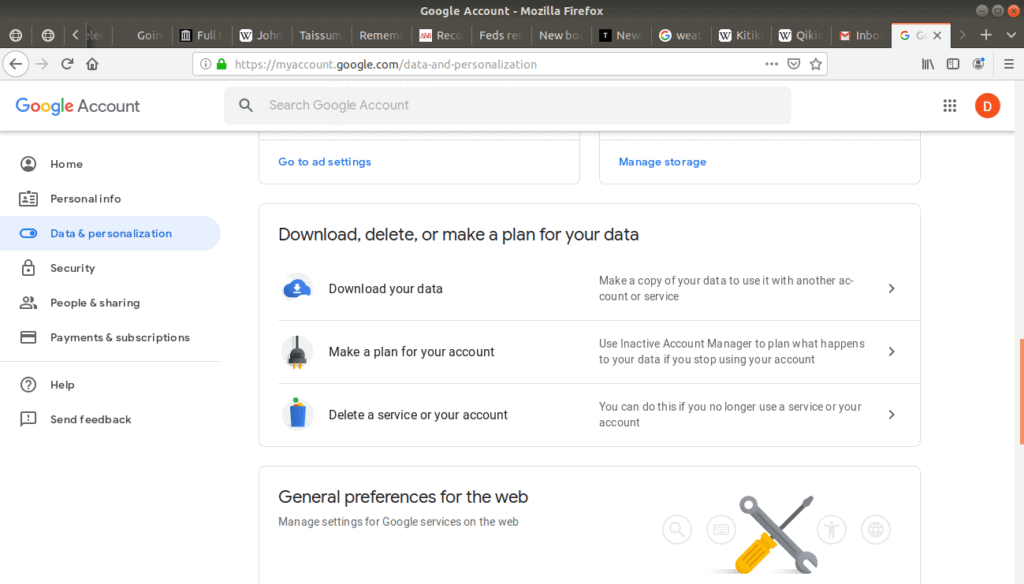
Advanced Tip: There’s also an option to Download your data? If you do decide to delete your account, it is a good idea to take this action first. Itsaves a copy of your email account to your own computer, making a backup of your information. This is valuable to have in case you want to restore your account at a later date.
On the next page is an option to Delete your Google Account:
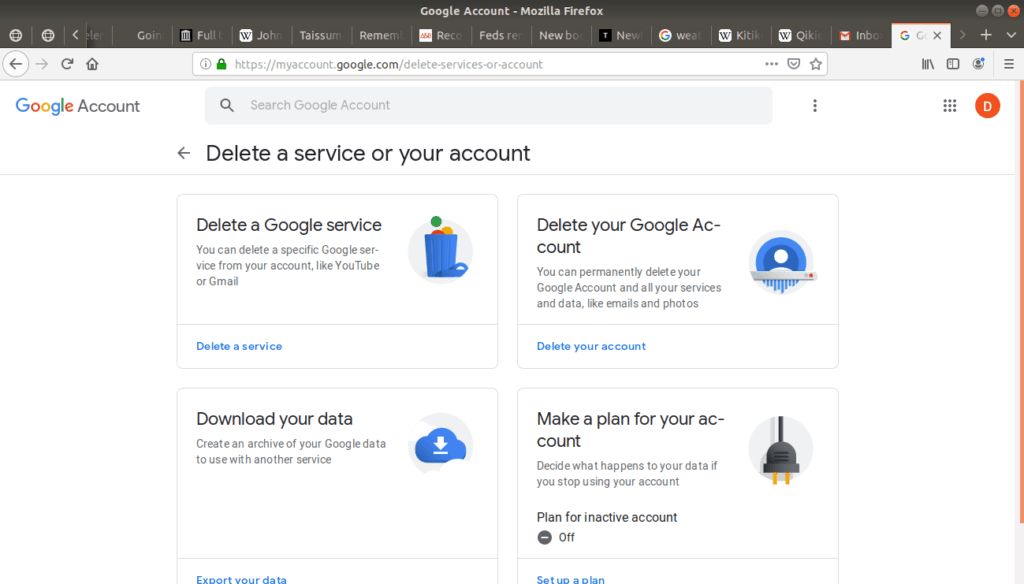
Tip: Even though online services provide the option to delete an account, they would prefer you didn’t, and will make you click through several links and menus to find the delete tool. If it’s hard to find the delete tool, a quick web search will often bring up advice or a tutorial about where to go to delete your account for a specific email provider.
Finally, when you open this tool you will be asked to enter your email address one last time:
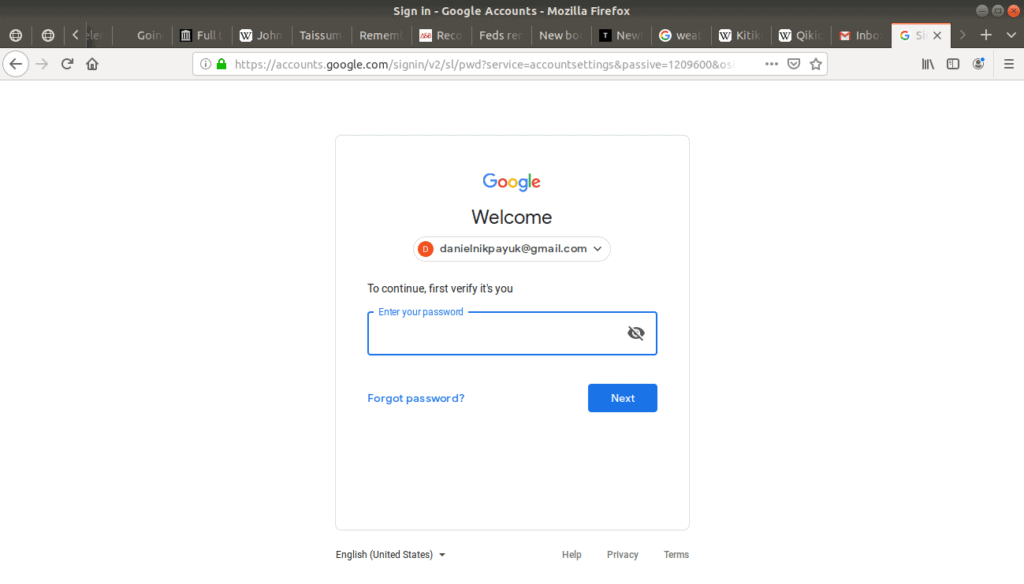
Deleting your account can have serious consequences because it means all of your emails will be deleted, so before your service provider deletes your account, they want to be absolutely certain you are who you say you are. After that, you should have one last screen which says your account has been deleted, as well as some other relevant information. And with that, your account is deleted.
Advanced Tip: Security experts have shown that many email (or other account) service providers leave your account on their computers even after they say they’ve deleted it. It’s not that they’re lying to you, but as businesses they want to save money, and deleting your account entirely from their systems costs money. The service provider will delete your information, but it sometimes happens months or years later.
If you want to be extra careful with your privacy, a security best practice is to change your personal account information to false information prior to deleting. For example, change the birthday and phone number on file to fake information. This way even if your account remains on their computers for a duration, it’s not accurate information about you.